
ZERO-DAY NETWORK SECURITY
DEPLOY ON CLOUD OR ON PREM.
REAL-TIME THREAT INTELLIGENCE
DEEP CONTENT INSPECTION TRANSPARENCY
ZERO-DAY NETWORK SECURITY
DEPLOY ON CLOUD OR ON PREM.
REAL-TIME THREAT INTELLIGENCE
DEEP CONTENT INSPECTION TRANSPARENCY
Product Overview
The Wedge Absolute Real-time Protection™ Series (WedgeARP) sets new industry benchmarks for performance and EverGreen Security™ with a family of virtualized and self orchestrated products to protect your network in real-time, with unbounded innovation.
Wedge Absolute Real-time Protection – WedgeARP™, has the deepest visibility of network data in the industry; possessing an unmatched ability to defend against malicious attacks that are undetectable with shallow inspection techniques. It delivers the highest real-time performance through a software implementation that is portable to all x86 servers.
Trained with nearly 1 billion threat samples, its automated and continually learning embedded artificial neural network can detect never-before-seen malware in milliseconds. As an orchestrated threat management platform, it is a novel approach that provides real-time large scale security implementations with effective threat management services.
Components of WedgeARP System
- WedgeIQ : Management Portal
- WedgeAMB: Advanced Malware Blocker
- WedgeMA: Malware Analyser
How It Works
At the heart of WedgeARP is Wedge’s patented Security Orchestrator (WedgeSO™). WedgeSO is the proverbial warp drive of the WedgeARP series. WedgeARP virtual or physical appliances are placed inline with the flow of traffic entering and leaving the enterprise network, data center, or partitioned sub network to inspect and secure data in motion.
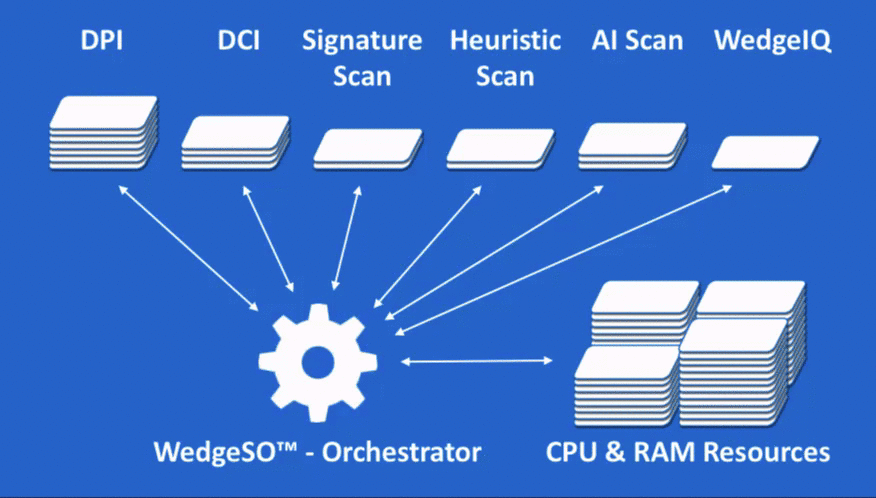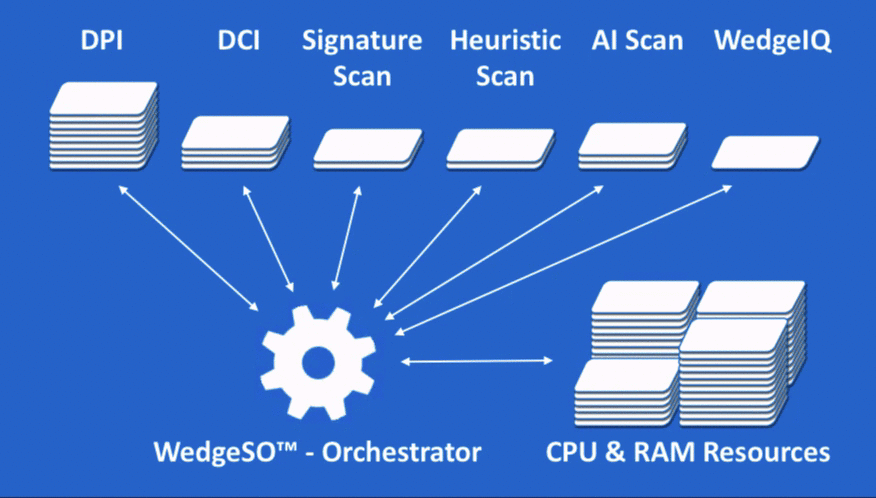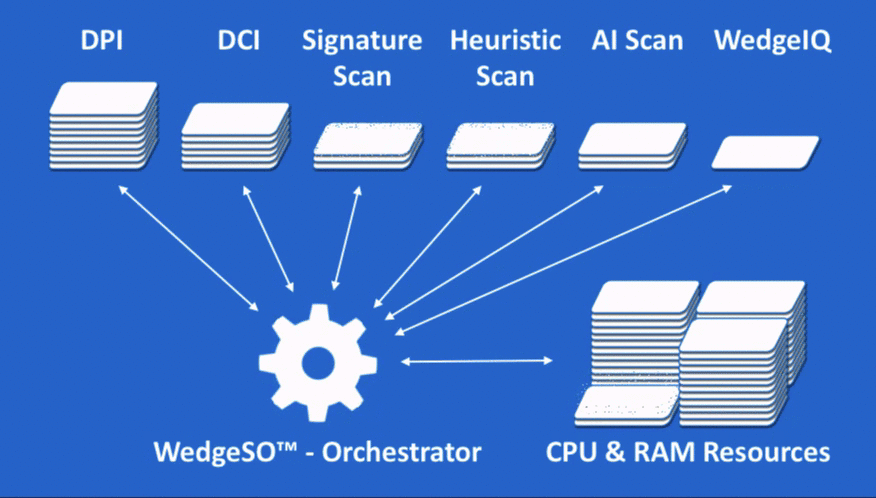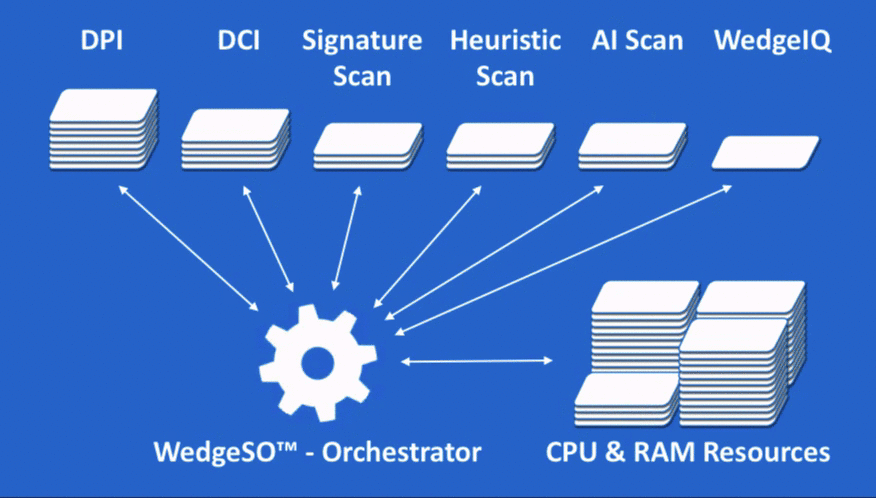
As traffic flows, the WedgeSO engine inspects packets and packet payloads and reconstructs the full file content in real-time using a combination of deep packet inspection (DPI) and deep content inspection (DCI). The content is then scanned and analysed with a series of virtualized network security functions which are subscribed to separately to provide specific security services. This real-time visibility to packets and fully reconstructed content sets the stage for accurate detection and blocking of conventional and advanced threats, as well as enforcement of specified security policies.





